Secure Remote Access: Integration with Network Firewall and Zero Trust
Remote work is no longer a flexibility option for employees working on-site. Most organizations are now shifting to a complete remote or hybrid work setting. In fact, a Gartner study reveals that 82% of company leaders plan to allow remote work at least part-time.
While that suggests a significant reduction in operational costs and greater flexibility for employees, it also comes with its own challenges. Remote work environments expand the attack surface of an organization and leave it open to cyber attackers.
Employees can now access sensitive information from their home networks, coffee shops, and mobile devices. It creates countless entry points for the attackers, making the company network vulnerable. Although traditional VPNs were once considered the safety net, they aren’t enough in today’s time. That’s why secure remote access is essential. A future-proof solution that combines perimeter defense with identity-based security is Essential.
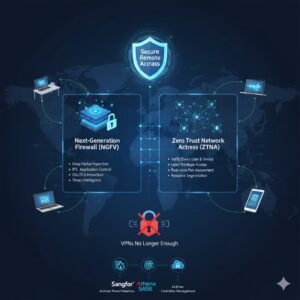
This is where Next-Generation Firewalls (NGFW) and Zero Trust Network Access (ZTNA) come together to deliver secure, scalable, and intelligent remote access.
Understanding Secure Remote Access
Secure remote access protocols ensure that authorized users can access network data and resources, regardless of their location or device. It provides users with access to a network while also ensuring sensitive data protection, prohibiting unauthorized users from accessing the network.
The goal of secure remote access is to maintain confidentiality, integrity, and availability while minimizing risks like credential theft, ransomware, and insider threats.
Why VPNs Are No Longer Enough
VPNs are no longer enough in today’s context. They provide broad and flat network access, leaving the network vulnerable to threats, and don’t fit the modern hybrid cloud environment. There’s a lack of granular and context-aware control. Most importantly, they don’t address risks associated with compromised credentials or devices.
The following are some common reasons why VPNs are no longer enough for your network’s security:
- Broad Access: VPNs usually provide full network access and increase lateral movement risk.
- Limited Visibility: IT teams struggle to monitor user activity effectively.
- Scalability Issues: VPN performance goes down with a large remote workforce.
- Static Trust Model: Once the users are connected to the network, they are trusted indefinitely. This is an open invitation to the attackers.
That’s why a context-aware and identity-driven approach to network access is necessary at the organizational level. Remote network access, as a strategy, often replaces or augments VPN with Zero Trust and NGFW integration to provide comprehensive endpoint protection. As a result, organizations with a significant number of endpoint users can’t simply leave endpoint protection to VPN.
Role of Network Firewalls in Remote Access
A Next-Generation Firewall (NGFW) is the cornerstone of modern-day network security. Unlike a traditional firewall, NGFW offers advanced capabilities.
Deep Packet Inspection: Malicious payloads stay hidden in the traffic. Deep packet inspection helps detect them.
Intrusion Prevention System (IPS): It is responsible for blocking known exploits and vulnerabilities.
Application Control: Restricts risky apps and enforces usage policies.
SSL/TLS Inspection: This inspection is responsible for securing encrypted traffic without affecting the performance.
Threat Intelligence Integration: Real-time updates are available from the global threat feeds.
Zero Trust: The Paradigm Shift
Zero trust isn’t a cybersecurity product. It’s a philosophy that depends on always verifying before blindly trusting. Instead of assuming trust within the network, Zero Trust continuously validates every single user, session, and device.
Core Principles of Zero Trust
The following are the core principles of this security philosophy that strengthen and ensure secure remote access solutions:
- There must be an authentication process for every user/ device before they are allowed to enter the network or access data.
- Provide permission to users only if the data is necessary for their task. That way, permission and access to data become task and responsibility-specific.
- Adapt policies depending on real-time risk assessment.
- Isolate resources to prevent lateral movement.
Integration of NGFW and Zero Trust for Secure Remote Access
A secure remote work environment nowadays depends on a holistic approach to your endpoint devices and users. That’s why the approach to integrate NGFW and Zero Trust is the best solution any cybersecurity provider could think of. In fact, leading managed IT security services providers like Sangfor integrate NGFW and Zero Trust for secure remote access.
This unified approach ensures consistent policy enforcement across application layers and the network, reducing complexity and improving resilience.
How Sangfor Achieves This: Athena Secure Access Service Edge (SASE)
For context, here’s how Sangfor relies on integrating network firewall and zero trust to ensure secure remote access:
- NGFW + Zero Trust Guard + Secure Access Service Edge (SASE): A holistic solution combining perimeter defense, identity-based access, and cloud security.
- AI-driven threat prevention: Detects anomalies and blocks attacks in real time.
- Centralized management: Simplifies policy configuration and monitoring.
Key Benefits of This Integrated Approach
Once integrated, network firewall and zero trust combine the following benefits for users:
- Enhanced Security Posture: Minimized lateral movement and real-time threat prevention.
- Operational Efficiency: Centralized management reduces complexity and cost.
- Scalability: Supports global enterprises with distributed teams.
- Improved User Experience: Faster, more secure access without VPN bottlenecks.
So! Are Your End Users Remotely Secure?
Secure remote access is no longer optional. With remote work and hybrid workforces terraforming industries, devices connecting to a company’s network from a remote location must be secure and encrypted with more than a VPN.
Secure remote access through the integration of network firewall and zero trust is nowadays a business imperative. By integrating Next-Generation Firewalls with Zero Trust principles, organizations can build a future-proof security architecture that protects against evolving threats.

